Adversary simulations – or red teaming – are among the most effective ways to test an organisation’s resilience to cyber threats. But these simulations aren’t just theoretical. They’re live exercises, often run in production environments, which means managing real risk – in real time.
At LRQA, we’ve developed a risk-led approach that allows us to simulate sophisticated attacks without compromising operations or trust. Here’s how we do it.
It starts with the Control Group
Every engagement begins with a dedicated Control Group – a team formed of key client stakeholders and LRQA consultants. This group stays informed at all times and plays a central role in planning, approvals and oversight throughout the exercise.
A risk workshop sets the tone. Together, we identify and assess:
- Operational risks for both red and blue team activities
- General project risks, including reputational and ethical considerations
- Legal and compliance risks
We also map these risks against four core management areas:
- Business insights – What do we need to protect and why?
- Crisis management – How and when do we escalate issues?
- Processes – What are the rules of engagement?
- Risk mitigation and acceptance – How do we treat or tolerate risk?
The strength of this group lies in its ability to align offensive testing with business priorities. By maintaining a continuous dialogue, both parties can adapt to new intelligence, respond to unexpected findings and ensure that every step remains in line with agreed outcomes. This relationship is the backbone of a safe and effective simulation.
The Control Group also enables clear lines of accountability. When everyone understands their role and risk ownership is shared, decisions can be made quickly – which is vital during fast-moving, real-time engagements.
Tiered risk model: Knowing what’s at stake
To protect critical operations, we use a tiered asset classification model, shaped during the risk workshop.
- Primary assets – Core systems like payment infrastructure or mainframes that directly support business-critical functions
- Secondary assets – Systems such as domain controllers, file servers and database platforms
- Tertiary assets – Non-critical environments like pre-production systems, desktops or virtual desktop infrastructure
This structure allows us to model risk exposure in a clear, consistent way. It ensures that every action taken during the simulation is proportionate to the value and sensitivity of the system being tested.
If, for example, the simulation targets a payment processing system, we might demonstrate the ability to compromise it without actually executing a full attack chain. Alternatively, if the client has a higher risk appetite, we can expand the scope – provided appropriate checks, approvals and contingency plans are in place.
At each stage, movement between asset tiers is strictly controlled. The goal is always the same: generate meaningful insight without causing unnecessary disruption.
Rules of engagement
Every LRQA adversary simulation is governed by a robust set of controls that are agreed upfront with the Control Group. These rules of engagement ensure risks are identified, owned and mitigated throughout the engagement.
These measures are not just risk-avoidance tactics – they are the foundation of trust in high-impact engagements. Without them, red teaming would risk becoming reckless rather than revealing. Each safeguard exists to protect operations, people and reputation.
Key safeguards include:
- Communications – The Control Group operates under NDA and maintains an out-of-band channel for secure, real-time coordination. This channel allows for immediate escalation if any unexpected behaviour is observed.
- Authorisations – Any lateral movement between asset tiers or action on objectives requires explicit approval from the Control Group. Nothing is assumed.
- Emergency stop – If an unrelated breach is identified during testing, or the client needs to halt activity, the simulation can be stopped instantly with full transparency.
- Vulnerabilities – High-risk vulnerabilities discovered during the engagement are not held back for the final report – they’re disclosed in real time, especially if they present a clear and credible path to compromise.
- Artefact removal – Once the engagement concludes, LRQA ensures that all red team artefacts are safely removed from the client environment, including implants, payloads and tool remnants.
- Denial of service – LRQA will never execute denial-of-service attacks during a live simulation. If a DoS condition is found, it is recorded without being triggered.
- Data protection – LRQA does not exfiltrate live production data unless explicit, written permission is provided.
- Implant safety – Implants are configured to execute only on domain-joined, in-scope assets. This ensures that even if payloads leave the environment, they will not function elsewhere.
- Third parties – Systems and infrastructure not owned or managed by the client are excluded from scope unless separately agreed.
- Escalations – A documented escalation process allows for quick resolution of any live concerns, particularly where blue teams may detect activity or become concerned about a possible incident.
Total visibility – without disruption
If a visual overlay to the engagement is desired, LRQA’s proprietary Engagement Dashboard is made available to all clients. It provides real-time insights into the simulation and is designed to give the Control Group 24/7 visibility without interfering with the live exercise.
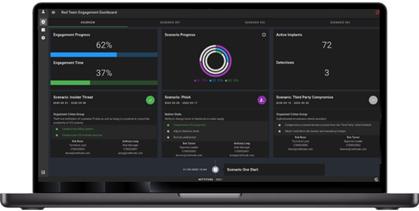
The dashboard shows:
- Live status of the simulated attack
- The number of active implants
- Scenario progress and key milestones
- A timeline of engagement activity to date
- An emergency stop button that halts all live activity instantly in the event of an incident or unrelated issue
Importantly, this is not a live stream of red team activity – the dashboard provides metadata only, designed for oversight, deconfliction and safe governance throughout the simulation.
Every command and action performed by the red team is logged in a central, immutable activity record – creating a forensically sound audit trail that covers the full scope of the engagement, from initial access to post-engagement clean-up.
The dashboard gives clients the ability to observe the simulation in real time – with full visibility, zero disruption and complete control
Looking ahead
This introduction offers a behind-the-scenes view of how we manage risk in live adversary simulations – from early-stage planning to active engagement. Whether the goal is to test resilience, support regulatory requirements or build confidence in your defences, risk management is the thread that holds it all together.
Every engagement teaches us something new – about technology, about people and about the evolving nature of risk. By capturing and applying those insights, we help clients not only defend but adapt.
At LRQA, we believe that resilience isn’t built by avoiding risk – it’s built by managing it, intelligently and transparently.
Learn more
LRQA supports organisations worldwide with tailored adversary simulation, cybersecurity assessments and incident response planning.
Contact us to find out how we can help










